How A-Dec works
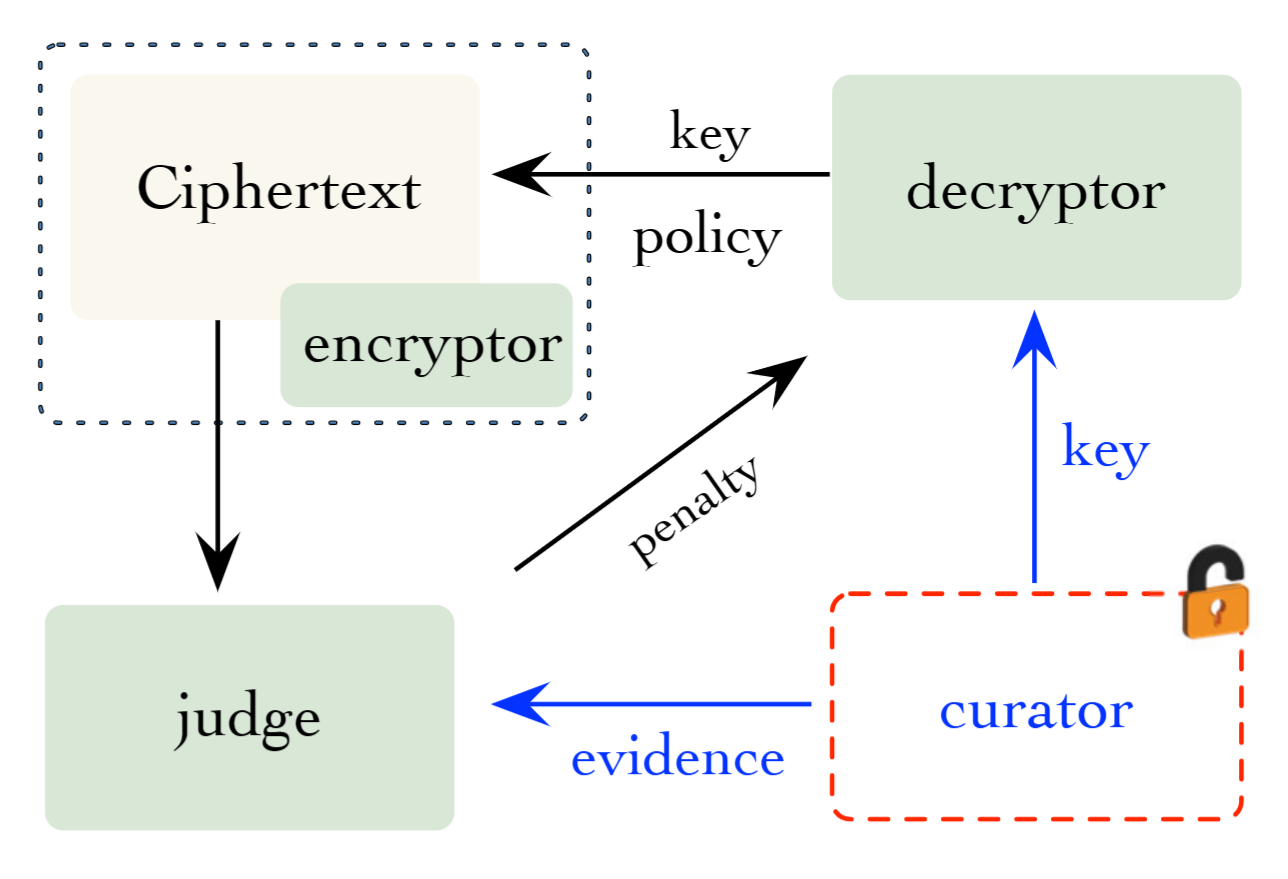
A-Dec is a process designed to ensure that users who create ciphertexts are aware of any subsequent decryption actions on the encrypted data. This process involves several key roles:
- Encryptor (E): This entity is responsible for creating ciphertexts.
- Decryptor (D): This entity is tasked with decrypting the ciphertexts.
- Judge (J): This entity is in charge of detecting any misbehavior during the decryption process. If the Decryptor (D) engages in such misbehavior, the Judge (J) imposes penalties, which can include measures such as deposit forfeiture and credit downgrade.
- Encryption
- Decryption
- Check
- Reaction
Encryption
An encryptor E executes the algorithm to generate a ciphertext ct, and policies P. Here, P dictates what are illegal actions, such as decryption at unpermitted time.
Decryption
A decryptor D runs this algorithm by taking as input a private key key and a ciphertext ct, the environment variables e, and outputs the plaintext m and a piece of evidence π for proving his decryption action.
Check
A judge J executes this algorithm to scrutinize the actions of the decryptor, ensuring compliance with the predefined policies. It takes as input the evidence of decryption π, the policy P and outputs a result tag ∈ {true, false}. Here, true indicates the decryptor's action is aligned with established policies.
Reaction
A judge J imposes penalties against the decryptor D who has conducted malicious decryption.
Security
Making TEE work in the “trust, but verify” model where a compromised state is detectable.
